Wurk SSL Certificates help
Get Started with SSL Certificates, a step-by step guide to request an SSL Certificate and install it.
Get started with SSL certificates
Generate a CSR (certificate signing request)
After you purchase an SSL certificate, and the credit is available in your account, you may need to generate a certificate signing request (CSR) for the website's domain name (or common name) before you can request the SSL certificate.
Note: If you're using an SSL certificate on the primary domain name of a Wurk shared hosting account, you do not need to generate a CSR; we take care of that for you.
How you generate a CSR depends on the type of certificate you're requesting and your operating system/control panel.
|
Type of Certificate |
Follow these instructions |
|
SSL Certificate |
You can generate a CSR on your server before you request an SSL certificate, or we can generate the CSR for you using the SSL Request Wizard. Click your server type for instructions: · cPanel · Apache · Nginx · Exchange Server 2016 · Microsoft IIS 10 · Cisco ASA 5500 VPN/Firewall · Google App Engine For other server types, see "more info" below. |
|
Code/driver signing |
Note: Starting June 1, 2021, Wurk will no longer issue or renew Code Signing or Driver Signing Certificates. If you already own a Code Signing or Driver Signing Certificate, you will be unable to rekey it after June 1, 2021. All certificates issued before June 1, 2021 will remain valid until they expire. |
Our certificates are compatible with all types of web servers, even if we do not have CSR instructions for them. Please consult your server documentation for further information on generating a CSR if you do not find the instructions that you need above.
Next step
After you create a CSR, you will need to request your certificate. How you request a certificate is dependent on the type of certificate you have:
|
Type |
Next step |
|
Standard, Deluxe or Extended Validation certificates |
Request my SSL certificate with a Certificate Signing Request (CSR) |
|
Code or Driver Signing certificates |
Note: Starting June 1, 2021, Wurk will no longer issue or renew Code Signing or Driver Signing Certificates. If you already own a Code Signing or Driver Signing Certificate, you will be unable to rekey it after June 1, 2021. All certificates issued before June 1, 2021 will remain valid until they expire. |
More info
Miscellaneous CSR instructions:
· Parallels Plesk Panel
· Microsoft IIS 8
· Microsoft IIS 7
· Exchange Server 2010
· Exchange Server 2013
- Install my SSL certificate
Required: This article is for customers that have already requested their SSL, downloaded their SSL files and are ready to install those files onto their server. If you haven’t done those things, here are some resources for you.
- If you have purchased an SSL certificate but have not requested it for your domain, go to Request my SSL certificate.
- If you're thinking about adding an SSL certificate to your site and want to learn about what it can do for you, take a look at Get an SSL certificate.
After you've downloaded your certificate files, you can install them on your server.
Note: If you do not see your server or specific OS version in this list, please refer to your server documentation to install your SSL and then Redirect HTTP to HTTPS automatically. Additionally, you may find third-party tools like Wappalyzer or DNSChecker or useful for identifying the server or specific operating system you are using.
If you're using Managed WordPress or Websites + Marketing, your SSL certificate is automatically installed for you.
SSL certificate installation instructions
Most popular servers
- cPanel
Not the right server type? Go back to the list of installation instructions
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your Web Hosting (cPanel) plan.
Required: Deluxe and extended validation (EV) certificates, as well as SSLs for
addon domains or subdomains must be installed manually.
Note: Want Wurk to install and maintain your SSL for you? Consider purchasing a Managed SSL.
- If you haven't done it already, download your certificate from the SSL manager and save the
.crtfile somewhere that's easy to find. - Go to your Wurk product page.
- Select Web Hosting and then select Manage for the Web Hosting (cPanel) plan you're installing the SSL on.
- Select cPanel Admin.
- In the Security section, select SSL/TLS.
- Under Certificates (CRT), select Generate, view, upload, or delete SSL certificates.
- In the Upload a New Certificate section, select Choose File and navigate to the
.crtfile you downloaded in step 1. Select the file and then select Open. - If you want to, type a description of the certificate in the Description text box.
- Select Upload Certificate.
- When you get confirmation that the certificate has been saved, select Go Back.
- At the bottom of the SSL Certificates page, select Return to SSL Manager.
- Under Install and Manage SSL for your site (HTTPS), select Manage SSL Sites.
- In the Install an SSL Website section, select Browse Certificates.
- Select the certificate that you want to activate and select Use Certificate. This will auto-fill the fields for the certificate.
- At the bottom of the page, select Install Certificate.
- On the Successfully Installed pop up, select OK.
Your certificate is installed! Now you need to direct visitors to the secure version of your site by redirecting to HTTPS.
- Apache (CentOS)
Not the right server type? Go back to the list of installation instructions
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your Apache server. If your server is running Ubuntu instead of CentOS, please see Manually install an SSL certificate on my Apache server (Ubuntu).
- Find the directory on your server where certificate and key files are stored, then upload your intermediate certificate (
gd_bundle.crtor similar) and primary certificate (.crtfile with randomized name) into that folder. - For security, you should make these files readable by root only.
- Find your Apache configuration file.
- On default configurations, you can find a file named
httpd.confin the/etc/httpdfolder. - If you have configured your server differently, you may be able to find the file with the following command:
grep -i -r "SSLCertificateFile" /etc/httpd/
/etc/httpd/may be replaced with the base directory of your Apache installation.- Open this file with your favourite text editor.
- Inside your
httpd.conffile, find the <VirtualHost> block. - To have your site available on both secure (https) and non-secure (http) connections, make a copy of this block and paste it directly below the existing <VirtualHost> block.
- You can now customize this copy of the <VirtualHost> block for secure connections. Here is an example configuration:
<VirtualHost xxx.xxx.x.x:443>
DocumentRoot /var/www/coolexample
ServerName coolexample.com www.coolexample.com
SSLEngine on
SSLCertificateFile /path/to/coolexample.crt
SSLCertificateKeyFile /path/to/privatekey.key
SSLCertificateChainFile /path/to/intermediate.crt
</VirtualHost>
- Don't forget the added 443 port at the end of your server IP.
- DocumentRoot and ServerName should match your original <VirtualHost> block.
- The remaining/path/to/... file locations can be replaced with your custom directory and file names.
- First, run the following command to check your Apache configuration file for errors:
apachectl configtest
- Confirm that the test returns a Syntax OK response. If it does not, review your configuration files.
Warning: The Apache service will not start again if your config files have syntax errors.
- After confirming a Syntax OK response, run the following command to restart Apache:
apachectl restart
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved.
- Apache (Ubuntu)
Not the right server type? Go back to the list of installation instructions
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your Apache server. If your server is running CentOS instead of Ubuntu, please see Manually install an SSL certificate on my Apache server (CentOS).
- Find the directory on your server where certificate and key files are stored, then upload your intermediate certificate (
gd_bundle.crtor similar) and primary certificate (.crtfile with randomized name) into that folder. - For security, you should make these files readable by root only.
- Find your Apache configuration file.
- On default configurations, you can find a file named
apache2.confin the/etc/apache2folder. - If you have configured your server differently, you may be able to find the file with the following command:
grep -i -r "SSLCertificateFile" /etc/apache2/
/etc/apache2/may be replaced with the base directory of your Apache installation.- Open this file with your favourite text editor.
- Inside your
apache2.conffile, find the < VirtualHost > block. - To have your site available on both secure (https) and non-secure (http) connections, make a copy of this block and paste it directly below the existing < VirtualHost > block.
- You can now customize this copy of the < VirtualHost > block for secure connections. Here is an example configuration:
<VirtualHost xxx.xxx.x.x:443>DocumentRoot /var/www/coolexample
ServerName coolexample.com www.coolexample.com SSLEngine on SSLCertificateFile /path/to/coolexample.crt SSLCertificateKeyFile /path/to/private key. Key SSL Certificate Chain File /path/to/intermediate.crt</VirtualHost>
- Don't forget the added
443port at the end of your server IP. - DocumentRoot and ServerName should match your original < VirtualHost > block.
- The remaining
/path/to/...file locations can be replaced with your custom directory and file names. - First, run the following command to check your Apache configuration file for errors:
apache2ctl configtest
- Confirm that the test returns a Syntax OK response. If it does not, review your configuration files.
Warning: The Apache service will not start again if your config files have syntax errors.
- After confirming a Syntax OK response, run the following command to restart Apache: apache2ctl restart
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved.
- Microsoft Exchange Server 2016
Not the right server type? Go back to the list of installation instructions.
After you request the certificate in our online application and it's ready for installation, you must download the files we provide.
First, you must install the intermediate certificate to your Microsoft® Exchange Server 2016. You also can download the intermediate certificate from the repository.
Then, to install the primary SSL certificate, you must complete the pending request, import the certificate file, and then select the services to which the certificate applies.
To Install an Intermediate Certificate in Microsoft Exchange Server 2016
- Click Start, and then click Run....
- Type mmc, and then click OK. The Microsoft Management Console (Console1) window opens.
- In the Console1 window, click File, and then select Add/Remove Snap-in.
- In the Add or Remove Snap-ins window, select Certificates, and then click Add.
- In the Computer Account window, select Computer Account, and then click Next.
- In the Select Computer window, select Local Computer, and then click Finish.
- In the Add or Remove Snap-ins window, click OK.
- In the Console1 window, click + to expand the Certificates (Local Computer)folder on the left.
- Right-click Intermediate Certification Authorities, mouse over All Tasks, and then click Import.
- In the Certificate Import Wizard window, click Next.
- Click Browse to find the intermediate certificate file.
- In the Open window, change the file extension filter to PKCS #7 Certificates (*.spc;*.p7b), select the *_iis_intermediates.p7b file, and then click Open.
- In the Certificate Import Wizard window, click Next.
- Select Place all certificates in the following store, and then click Browse.
- In the Select Certificate Store window, select Intermediate Certification Authorities, and then click OK.
- In the Certificate Import Wizard window, click Next.
- Click Finish.
- Click OK.
- Close the Console1 window, and then click No to remove the console settings.
To Install an SSL Certificate in Microsoft Exchange Server 2016
- Log in to the Exchange Admin Centre.
- From the left menu, select Servers, and then click Certificates.
- Select your certificate (it has a “Pending request” status), and then click Complete.
- For File to import from, enter the certificate file path we provided (such as \\server\folder\coolexample.crt), and then click OK. Exchange installs your certificate.
- In the Certificates section, select your certificate again (the status changed to “Valid”), and then click Edit (pencil icon).
- Click Services, select the services to which the certificate applies (SMTP, UM, UM call router, IMAP, POP, and/or IIS), and then click OK. Your certificate is now ready to use with Exchange 2016.
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved.
- Microsoft IIS 10
Not the right server type? Go back to the list of installation instructions.
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your IIS 10 server.
Convert your .crt file to a .cer file
- Locate your downloaded
.crtfile, and double-click to open it. - Select the Details tab, and then the Copy to File button.
- Select Next in the Certificate Wizard.
- Select Base-64 encoded X.509(.CER) and then select Next.
- Select Browse, locate where you want to save your
.CERfile, and type in a name for your certificate. - Select Next and then Finished.
Copy your certificate files onto the server
- Find the directory on your server where certificate and key files are stored, then upload your intermediate certificate (
gd_iis_intermediates.p7bor similar) and primary certificate (.cerfile that you just converted) into that folder.
Add a Certificate Snap-in to the Microsoft Management Console (MMC)
- Click on your Start Menu, then click Run.
- In the prompt, type mmc and click OK.
- Click File, then click Add/Remove Snap-in.
- On the new window, click the Add button.
- On the new window, select Certificates and click Add.
- Select Computer account for the snap-in and click Next.
- Click Local computer and click Finish.
- Click Close on the Add Standalone Snap-in window.
- Click OK on the Add/Remove Snap-in window.
Import the Intermediate SSL Certificate
- In the MCC Console, click ▸ to expand Certificates (Local Computer).
- Right click on the Intermediate Certification Authorities folder, hover over All Tasks and click Import.
- On the new window, click Next.
- Click Browse, find your
gd_iis_intermediates.p7bintermediate certificate file and click Open. - Click Next, verify that the certificate information is proper and click Finish.
- Close the the import was successful notification.
Install your SSL certificate
- Click on your Start Menu, then click Run.
- In the prompt, type inetmgr and click OK to launch the Internet Information Services (IIS) Manager.
- Under the Connections panel on the left, click on your Server Name.
- In the main panel under the IIS section, double click on Server Certificates.
- Under the Actions panel on the right, click Complete Certificate Request.
- On the new window, click ... to browse, find your previously uploaded primary certificate file and click Open.
- Add a Friendly name to easily identify this certificate in the future.
- In the certificate store option, select Web Hosting and click OK.
Bind the SSL certificate
- Under the Connections panel on the left, click ▸ to expand the Sites folder.
- Click the Site Name that you plan to install the SSL certificate onto.
- Under the Actions panel on the right, find the Edit Site section and click Bindings.
- On the new window, click Add and fill out the following information:
- Type: select https.
- IP Address: select All Unassigned.
- Port: type in 443.
- Host name: leave this empty.
- SSL Certificate: select your recently installed SSL.
- Click OK to confirm, then Close for the Site Bindings window.
Restart IIS (optional)
- Under the Actions panel on the right, find the Manage Website section and click Restart.
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved
- Microsoft IIS 8
Not the right server type? Go back to the list of installation instructions
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your IIS 8 server.
Copy your certificate files onto the server
- Find the directory on your server where certificate and key files are stored, then upload your intermediate certificate (
gd_iis_intermediates.p7bor similar) and primary certificate (.crtfile with randomized name) into that folder.
Add a Certificate Snap-in to the Microsoft Management Console (MMC)
- Click on your Start Menu, then click Run.
- In the prompt, type mmc and click OK.
- Click File, then click Add/Remove Snap-in.
- On the new window, click the Add button.
- On the new window, select Certificates and click Add.
- Select Computer account for the snap-in and click Next.
- Click Local computer and click Finish.
- Click Close on the Add Standalone Snap-in window.
- Click OK on the Add/Remove Snap-in window.
Import the Intermediate SSL Certificate
- In the MCC Console, click ▸ to expand Certificates (Local Computer).
- Right click on the Intermediate Certification Authorities folder, hover over All Tasks and click Import.
- On the new window, click Next.
- Click Browse, find your previously uploaded intermediate certificate file and click Open.
- Click Next, verify that the certificate information is proper and click Finish.
- Close the the import was successful notification.
Install your SSL certificate
- Click on your Start Menu, then click Run.
- In the prompt, type inetmgr and click OK to launch the Internet Information Services (IIS) Manager.
- Under the Connections panel on the left, click on your Server Name.
- In the main panel under the IIS section, double click on Server Certificates.
- Under the Actions panel on the right, click Complete Certificate Request.
- On the new window, click ... to browse, find your previously uploaded primary certificate file and click Open.
- Add a Friendly name to easily identify this certificate in the future.
- In the certificate store option, select Personal and click OK.
Bind the SSL certificate
- Under the Connections panel on the left, click ▸ to expand the Sites folder.
- Click the Site Name that you plan to install the SSL certificate onto.
- Under the Actions panel on the right, find the Edit Site section and click Bindings.
- On the new window, click Add and fill out the following information:
- Type: select https.
- IP Address: select All Unassigned.
- Port: type in 443.
- Host name: leave this empty.
- SSL Certificate: select your recently installed SSL.
- Click OK to confirm, then Close for the Site Bindings window.
Restart IIS
- Under the Actions panel on the right, find the Manage Website section and click Restart.
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved.
- Microsoft IIS 7
Not the right server type? Go back to the list of installation instructions.
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your IIS 7 server.
Copy your certificate files onto the server
- Find the directory on your server where certificate and key files are stored, then upload your intermediate certificate (
gd_iis_intermediates.p7bor similar) and primary certificate (.crtfile with randomized name) into that folder.
Add a Certificate Snap-in to the Microsoft Management Console (MMC)
- Click on your Start Menu, then click Run.
- In the prompt, type mmc and click OK.
- Click File, then click Add/Remove Snap-in.
- On the new window, click the Add button.
- On the new window, select Certificates and click Add.
- Select Computer account for the snap-in and click Next.
- Click Local computer and click Finish.
- Click Close on the Add Standalone Snap-in window.
- Click OK on the Add/Remove Snap-in window.
Import the Intermediate SSL Certificate
- In the MCC Console, click ▸ to expand Certificates (Local Computer).
- Right click on the Intermediate Certification Authorities folder, hover over All Tasks and click Import.
- On the new window, click Next.
- Click Browse, find your previously uploaded intermediate certificate file and click Open.
- Click Next, verify that the certificate information is proper and click Finish.
- Close the the import was successful notification.
Install your SSL certificate
- Click on your Start Menu, then click Run.
- In the prompt, type inetmgr and click OK to launch the Internet Information Services (IIS) Manager.
- Under the Connections panel on the left, click on your Server Name.
- In the main panel under the IIS section, double click on Server Certificates.
- Under the Actions panel on the right, click Complete Certificate Request.
- On the new window, click ... to browse, find your previously uploaded primary certificate file and click Open.
- Add a Friendly name to easily identify this certificate in the future.
- Click OK.
Bind the SSL certificate
- Under the Connections panel on the left, click ▸ to expand the Sites folder.
- Click the Site Name that you plan to install the SSL certificate onto.
- Under the Actions panel on the right, find the Edit Site section and click Bindings.
- On the new window, click Add and fill out the following information:
- Type: select https.
- IP Address: select All Unassigned.
- Port: type in 443.
- Host name: leave this empty.
- SSL Certificate: select your recently installed SSL.
- Click OK to confirm, then Close for the Site Bindings window.
Restart IIS
- Under the Actions panel on the right, find the Manage Website section and click Restart.
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved.
Others
- AWS SERVER
Not the right server type? Go back to the list of installations instructions.
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your Amazon Web Services (AWS) server. This guide focuses on the Application Load Balancer (ALB)within the Elastic Load Balancer (ELB) platform.
Note:
• You can generate a certificate signing request (CSR) on your Elastic Compute Cloud (EC2) instance. There are multiple ways to do this. Check your server documentation for more information.
• If you're utilizing the Elastic Container Service (ECS), you'll want to connect to your Windows. or Linuxinstance and install the certificate manually.
- Sign in to your Amazon EC2 console at https://console.aws.amazon.com/ec2.
- In the Navigation menu on the left, expand NETWORK & SECURITY and select Load Balancers.
- In the main panel, select the load balancer where you wish to upload your certificate.
- In the new section below, click on the Listeners tab.
- Click Change in the SSL Certificate column for your HTTPS (Secure HTTP)Load Balancer Protocol.
- In the new Select Certificate window, click the radio button for Upload a new SSL certificate to AWS Identity and Access Management (IAM).
- For Certificate Name, type in a name that will allow you to easily identify your SSL at a later date
- For the Private Key field, simply paste the text from your
coolexample.com.keyfile. - This should include the "-----BEGIN RSA PRIVATE KEY-----" and "-----END RSA PRIVATE KEY-----" lines.
- For the Public Key Certificate field, simply paste the text from your randomly named
.crtfile. - Be sure to should include the "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----" lines.
- For the Certificate Chain field, simply paste the text from your
gd_bundle.crt(or similar) file. - Be sure to should include the "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----" lines.
- You should have a total of three certificate bundles in this text field.
- Click the blue Save button to finalize your SSL install.
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved.
- Microsoft Azure Web App
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your Microsoft IIS Server. Once the certificate is installed on your IIS server, follow this guide to convert the certificate to a .pfxfile and upload it to your Microsoft Azure Portal.
If you are utilizing an Azure Virtual Machine instead of an Azure Web App, you will want to connect to your instance and install the certificate manually.
- Click on your Start Menu, then click Run.
- In the puallyrompt, type inetmgr and click OK to launch the Internet Information Services (IIS) Manager.
- Under the Connections panel on the left, click on your Server Name.
- In the main panel under the IIS section, double click on Server Certificates.
- Select your recently installed certificate.
- Under the Actions panel on the right, click Export....
- In the new window, click ... under the Export to: section.
- Find the directory on your server where certificate and key files are stored, then type out your desired File name. Click Open.
- For the Password and Confirm password fields, type in a password to secure the file. This will be used when uploading the file to Azure.
- Click OK to create the
.pfxfile. - Sign in to your Azure portal at https://portal.azure.com.
- On the left sidebar, click App Services and select your app in the new listing column that appears.
- On the left sidebar within your application area, find the SETTINGS grouping and click SSL certificates.
- In the new SSL area, click Upload Certificate.
- On the Add certificate sidebar to the right, click the folder icon to browse and select your
.pfxfile and click Open. - Type out your password for the
.pfxfile in the Certificate password field and click Submit. - In the main SSL area, click Add binding below your new certificate.
- On the Add SSL Binding sidebar to the right, select your Hostname and Certificate.
- Choose SNI SSL for SSL Type and click Add Binding to finalize the SSL install.
Next steps
- Use our Certificate Checker to confirm the SSL is installed.
- Redirect your web app to HTTPS with a web.config file.
More info
- Renewing your SSL certificate.
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved.
Manually install an SSL certificate on my Cisco ASA 5500 VPN/Firewall
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your Cisco Adaptive Security Appliance (ASA) 5500 VPN or firewall.
- Find the directory on your server where certificate and key files are stored, then upload your intermediate certificate (
gd_bundle.crtor similar) and primary certificate (.crtfile with randomized name) into that folder. - Launch the Cisco ASDM (Adaptive Security Device Manager).
- In the list of icons near the top of the screen, click Configuration.
- On the left hand sidebar, click Remote Access VPN.
- In the new panel on the left, click to expand Certificate Management and click CA Certificates.
- On the right-hand side of the main panel, click Add.
- For the Trustpoint Name, simply enter a name to easily identify your intermediate certificate at a later date.
- Select the radio button to Install from a file and click Browse....
- Select your recently uploaded
gd_bundle.crt(or similar) file and click OK. - Click Install Certificate to install the intermediate certificate.
- In the panel on the left, locate the expanded Certificate Management section and click Identity Certificates.
- Select your recently installed intermediate certificate, which will show Not Available for Issued By and Pending for Expiry Date.
- On the right-hand side of the main panel, click Install.
- Select the radio button to Install from a file and click Browse....
- Select your recently uploaded primary certificate (randomly named
.crtfile) and click OK. - Click Install Certificate.
- Click OK to close the success message.
- Back in the Cisco ASDM, find the panel on the left. Click to expand Advanced and click SSL Settings.
- In the Certificates section, select the interface used to terminate WebVPN sessions and click Edit.
- For Primary Enrolled Certificate, select your newly installed SSL from the drop down menu and click OK.
- Click Apply to finalize the settings for WebVPN sessions that terminate on your selected interface.
Next step
- Use our Certificate Checker to confirm the SSL is installed.
More info
- Renewing your SSL certificate
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved.
Manually install an SSL certificate on my Google App Engine
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your Google App Engine inside the Google Cloud Platform.
If you're utilizing the Google Compute Engine instead of the Google App Engine, you'll want to connect to your instance and install the certificate manually.
- Sign in to your Google Cloud Platform account at https://console.cloud.google.com.
- In the Navigation menu on the left, select App Engine.
- Under App Engine on the left panel, click Settings.
- In the main section, click the SSL Certificates menu at the top.
- Click the blue Upload a new certificate button.
- On the new window, enter a name that will allow you to easily identify your SSL at a later date in the Name field.
- For the public key certificate field, simply paste the text from your randomly named
.crtfile, then in a new line paste the text from yourgd_bundle.crt(or similar) file. - Be sure to should include the "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----" lines.
- You should have a total of four certificate bundles between the two files in this text field.
- For the private key field, simply paste the text from your
coolexample.com.keyfile. - This should include the "-----BEGIN RSA PRIVATE KEY-----" and "-----END RSA PRIVATE KEY-----" lines.
- Click the blue Upload button.
- On the Edit Certificate page, find the Enable SSL for the following custom domains section.
- Check the boxes for the domains you are securing with your certificate.
- Click the blue Save button at the top of the page to finalize the SSL install.
Next steps
- Use our Certificate Checker to confirm the SSL is installed.
- Redirect your web app to HTTPS
More info
- Renewing your SSL certificate.
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved.
Intel vPro: certificate info
If you are using an Intel® vPro server, purchase a Deluxe SSL certificate and specify that it is for vPro during the application process.
Note: If you do not see the option to purchase a Deluxe SSL, contact customer support.
When purchasing a Deluxe SSL for a vPro server, select one of the following options:
- Single Domain for a single domain environment.
- Single Domains with Unlimited Subdomains (wildcards are supported for AMT 2.6 / 3.2 and higher).
Generating a Certificate Signing Request
Before you apply for the certificate you must first generate and submit a Certificate Signing Request (CSR). Your Web server software generates the CSR and creates the public/private key pair that you will use to encrypt and decrypt secure transactions.
Note: It is not necessary to specify a department or organizational unit (OU) when generating a CSR.
For more information, see CSR Generation Instructions.
Applying for a Certificate
During the application process, specify that this certificate is for use with Intel vPro. This selection adds the required Intel vPro provision to your certificate.
Download the SSL Certificate
After your application is approved, you'll need to download your certificate files. When selecting your server type, select Other. The bundle of files this downloads includes an intermediate and a cross certificate; you must install both of these to ensure your certificate works properly.
After downloading the bundle, see Install my SSL certificate.
Manually install an SSL certificate on my Exchange Server 2013
After your certificate request is approved, you can download your certificate from the SSL manager and install it on your Microsoft Exchange Server 2013.
Copy your certificate files onto the server
- Open the Exchange server's network share folder where your certificate and key files are stored, then upload your intermediate certificate (
gd_iis_intermediates.p7bor similar) and primary certificate (.crtfile with randomized name) into that folder.
Add a Certificate Snap-in to the Microsoft Management Console (MMC)
- Click on your Start Menu, then click Run.
- In the prompt, type mmc and click OK.
- Click File, then click Add/Remove Snap-in.
- On the new window, click the Add button.
- On the new window, select Certificates and click Add.
- Select Computer account for the snap-in and click Next.
- Click Local computer and click Finish.
- Click Close on the Add Standalone Snap-in window.
- Click OK on the Add/Remove Snap-in window.
Import the Intermediate Certificate Authority Certificate
- In the MCC Console, click ▸ to expand Certificates (Local Computer).
- Right click on the Intermediate Certification Authorities folder, hover over All Tasks and click Import.
- On the new window, click Next.
- Click Browse, find your previously uploaded intermediate certificate file and click Open.
- Click Next, verify that the certificate information is proper and click Finish.
- Close the the import was successful notification.
Install your SSL with the Exchange Admin Centre
- Access the Exchange Admin Centre by opening a web browser and visiting https://localhost/ecp
- Log into your account with the Domain\user format for your username and the related password.
- On the left side bar, select Servers.
- At the end of top menu in the main section, select Certificates.
- Select your certificate with a status of Pending request in the main panel. This can be identified by the friendly name you chose when generating the CSR.
- On the right column, find the Status section and click Complete.
- On the new window, type out the network share folder's path and your
.crtfile name in the File to import from field and click ok.
Enable your SSL certificate
- In the main panel of the Certificates page, select your certificate with a status of Valid.
- Above the list of certificates, click the pencil icon to edit your certificate.
- On the new window, find the exchangecert section to the left and click Services.
- Select the services where you want the certificate enabled (for example: SMTP, IMAP, POP and IIS).
- Click save.
Next step
- Use our Certificate Checker to confirm the SSL is installed.
More info
- Renewing your SSL certificate
Note: As a courtesy, we provide information about how to use certain third-party products, but we do not endorse or directly support third-party products and we are not responsible for the functions or reliability of such products. Third-party marks and logos are registered trademarks of their respective owners. All rights reserved.
NGINX: Install a certificate
After your certificate request is approved, you can download your SSL and intermediate certificates from the SSL application. For more information see Downloading Your SSL Certificate. These files must be installed on your Web server.
You can also download the intermediate certificate bundle from the repository
To Install SSL and Intermediate Certificates
- Copy your SSL certificate file and the certificate bundle file to your Nginx server.
- You should already have a key file on the server from when you generated your certificate request.
- Edit your Nginx configuration to reference these files. The exact configuration file you edit depends on your version of Nginx, your OS platform, or the method used to install Nginx.
Your SSL Certificate is installed. If you have problems, please see Test your SSL’s configuration to help diagnose issues.
For more information on how to configure your Nginx server, see http://nginx.org/en/docs/http/confuring_https_servers.html#chains.
NGINX on CentOS 7: Install a Certificate
After your certificate request is approved, you can download your SSL and intermediate certificates from the SSL application. For more information see Downloading Your SSL Certificate. You will want to select the Apache option when you download your certificate.
Note: This SSL installation was done on a CentOS 7 server with a LEMP stack installed. The exact configuration of your server may be different, based on your version of Nginx, your OS platform, or the method used to install Nginx.
- Connect to your server via SSH.
- Create a directory to store the server key, certificate, and intermediate bundle.
sudo mkdir /etc/nginx/ssl
- Copy your private key which was created when you generated your CSR to the ssl folder
cp coolexample.key /etc/nginx/ssl
- SFTP to your server, and upload your SSL certificate and intermediate bundle to the /etc/nginx/ssl folder.
- Navigate to the SSL folder in SSH.
cd /etc/nginx/ssl
- Combine your SSL certificate and the intermediate bundle into one file using the concatenate command. Since your intermediate certificate and root certificate come in a bundle, you can use the following SSH command:
sudo cat f84e19a2f44c6386.crt gd_bundle-g2-g1.crt >> coolexample.crt
Note: The certificates have to be listed in this order with the concatenate command or the SSL will not work properly on your server.
- Open your NGINX config file for the domain you're installing the SSL certificate to.
sudo vim /etc/nginx/sites-available/coolexample.com - Update the config file to use the SSL certificate.
9. server {listen 80;server_name coolexample.com; return 301 https://$host$request_uri;}server {listen 443 ssl;server_name coolexample.com; ssl_certifica /etc/nginx/ssl/coolexample.crt; ssl_certificate_key /etc/nginx/ssl/coolexample.key;roo/usr/share/nginx/coolexample.com/;index index.php index.html index.htm;}
- Save the config file. wq!
- Restart your NGINX server. sudo service nginx restart
Plesk: Install a certificate
Follow the instructions below to install the SSL certificate on your Web server. When you have completed the installation process, you must restart Parallels Plesk Panel so that your server will recognize the new certificate.
About the Intermediate Certificate
Before you install your issued SSL certificate, you must install our intermediate certificate on your Web server. Intermediate certificates provide an added level of security because the Certification Authority (CA) does not need to issue certificates directly from the CA root certificate.
An intermediate certificate is a subordinate certificate issued by the trusted root specifically to issue end-entity server certificates. The result is a trust-chain that begins at the trusted root CA, through the intermediate, and finally ending with the SSL certificate issued to you. Such certificates are called "chained root certificates."
You can download the intermediate/root certificate bundle from our repository
After you download the bundled certificate, intermediate certificate, and your issued SSL certificate, install all of the files on your Web server. For more information, see Download my SSL certificate files.
To Install SSL and Intermediate Certificates in Parallels Plesk Panel 17 & 18
- Log in to Parallels Plesk Panel as admin.
- If necessary, switch to Service Provider view.
- From the Hosting Services menu, select Domains.
- Select on the domain name that the certificate is issued for.
- On the Dashboard, select SSL/TLS Certificates.
- Under Download or remove existing certificates select Manage.
- Under Name, select the certificate you want to use.
- Next to the Certificate (*.crt) field, select Browse.
- Locate your signed CRT file, such as 123456789.crt, and then select Open.
- Next to the CA certificate (*-ca.crt) field, select Browse.
- Locate the certificate bundle, and then select Open.
- Select Upload Certificate.
- Go back to the Dashboard for your domain, and then select the Hosting & DNS tab.
- select Hosting Settings.
- Make sure that Enable SSL support is selected, and then select your SSL certificate from the menu.
- Select OK.
- If your server is running Linux, stop and start the Apache process. If your server is running Windows, stop and start the IIS service.
Your SSL certificate should now be installed. If you have problems, see Test your SSL’s configuration to help diagnose issues.
Manage your SSL certificate
What to do after your certificate is installed?
· Test your SSL’s configuration
Test your SSL's configuration
The process of getting an SSL issued and installed can be complicated, but there are tools available to help you get through it.
After you generate a certificate signing request (CSR), you can paste it into CSR decoder to make sure you have the correct common name and organization listed in the CSR from your server. If the information shown on the CSR decoder isn't correct, you can repeat the process of generating a CSR with the correct common name and organization.
Note: If the CSR you are using is for a wildcard certificate, the CSR must include the asterisk for the sub-domain level you wish to cover on the common name. Example: To secure test.coolexample.com and www.coolexample.com, the common name on your CSR needs to be *.coolexample.com
After you have installed your SSL certificate, you can use our SSL checker test tool to view the details on your certificate and check for a variety of common SSL issues. Most issues that come up on the certificate checker can be solved by rekeying your certificate and installing it again.
More info
- Generate a CSR (certificate signing request)
- Install SSL certificates
Renewing my SSL Certificate
When your SSL certificate isn’t set to auto-renew, you have a 90-day window to purchase a renewal credit and apply it to the certificate. The window goes from 60 days before to 30 days after the expiration date.
Note: If your certificate is set to auto-renew, we will renew it 60 days prior to the certificate's expiration date. This ensures you have time to complete the verification process. Verification must occur before your certificate expires, or you risk potential disruptions to your site and business. Although you're renewing early, the renewal period starts immediately after your current subscription ends, ensuring continuity of service.
Warning: If you haven’t completed the renewal by the expiration date, your website displays an error message and won't be accessible to your visitors.
If you’re using a Domain Validation (DV) certificate with the primary domain for your account, and you’ve set the certificate to auto-renew, no further action is needed on your part. Renewing your SSL certificate is completely automated.
For all other certificates, including certificates for an add-on domain, follow these steps.
- Go to your Wurk product page.
- Select SSL Certificates and do one of the following for the certificate you want to renew:
- If the billing for your renewal is already completed, skip to the next step.
- If you don't have auto-renew, select Renew if you don't have auto renew. If you have auto-renew, select Renew now.
- Select the certificate you want to renew, select Continue to Cart, and complete the transaction for your renewal.
If this was your primary domain and your site is hosted with us, you’re done! We’ll install your renewed certificate for you. If your site is hosted with a third party or this is for an add-on domain, you need to install the renewed certificate. For help, see Install my SSL certificate.
More info
- Rekey my certificate
- Change the domain name (common name) on my. SSL certificate
- Compare SSL plans and pricing
Turn off auto-renew
Turn off auto-renew and cancel subscriptions for your products. When you cancel renewal for a product, your subscription will end and you won’t be charged on the next billing date. If you change your mind, you can manually renew the product.
Note: If you purchased your product through a mobile app store like the Apple App Store or Google Play, you need to use that mobile app store to make changes to your subscription.
- Go to your Wurk Renewals & Billing page. You might be prompted to sign in.
- Next to your product or domain, select the checkbox.

- Turning off auto-renew for a subscription with multiple products will apply to all products in the subscription. The products cannot be individually changed.
- At the top of the page, select Cancel Renewal.
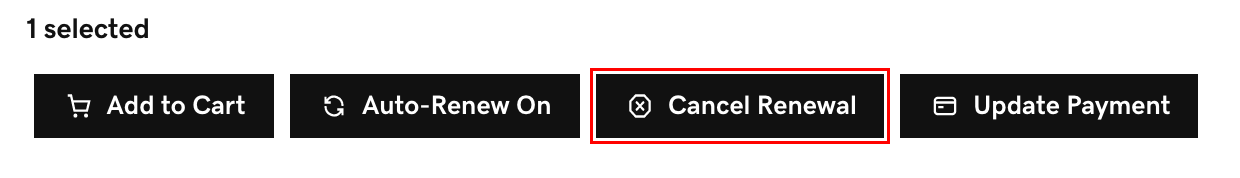
- A new window will appear. Select Cancel Renewal, and we'll confirm that automatic renewal has been cancelled.
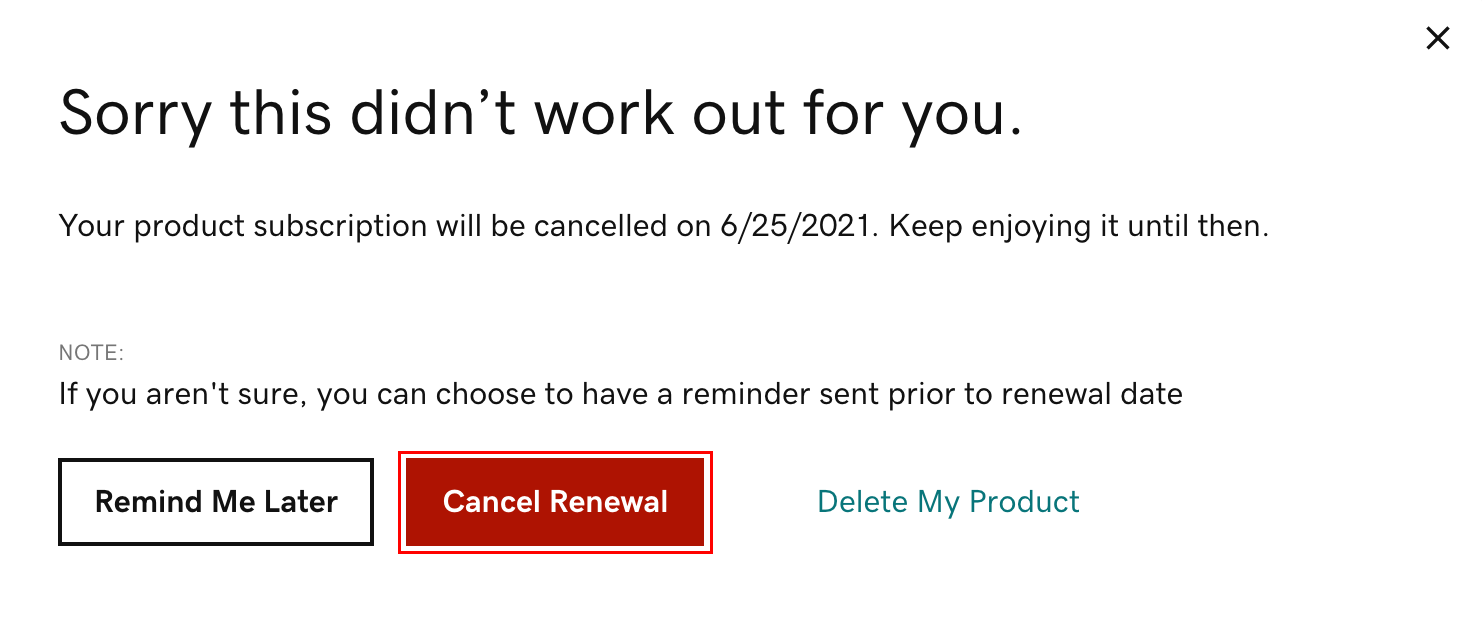
Note: If you’re cancelling a domain with Domain Protection, we'll need to verify your identity. Select Yes, Delete this product, then select Verify and delete. We'll send a verification code via SMS text message or authenticator app if you've had 2-step verification (2SV) enabled in your account for more than 24 hours. Otherwise, select Send Password to send a one-time password to your registrant email address.
When renewal is cancelled, the Billing Date column shows the date your product subscription ends. You can keep using the product until the end date.
Warning: If you don't manually renew the product before the end of your subscription, the product will be removed from your account and might not be recoverable.
Related step
- If you change your mind, you can manually renew your product.
More info
- If you can't turn off auto-renew for a domain, it's possible that the domain status is pending updates. Domains must be in active status before you can change the auto-renew setting.
- If a domain doesn't work out, you can delete a domain from your account.
- If a product (other than a domain) doesn't work out, you can delete the product from your account.
- To find out if you're eligible for a refund, contact our Wurk Guides for help.
- Here's our refund policy.
Rekey my certificate
Note: Managed WordPress plans come with an integrated SSL certificate.
- The integrated SSL certificate - This SSL is automatically installed when you attach your domain. No further action is needed on your part.
- A standalone SSL certificate - An SSL purchased separately from your Managed WordPress plan. Follow the directions in the Re-key my Managed WordPress standardalone SSL certificate article.
You should re-key your SSL certificate when:
- You change the domain name (common name) of your SSL.
- You want to change your SSL certificate's issuing organization. For more information, see Using the Right Issuing Organization for Your SSL.
- Your server crashes.
- You lose your private key.
- You move your website to a new server.
Required:
- Before you can re-key your SSL certificate, you must generate a new certificate signing request (CSR) from your Web server. For instructions, see Generate a CSR (certificate signing request).
- Don't revoke unless you are certain you want to cancel the existing certificate. When you revoke, the SSL credit is cancelled and you can't re-key the certificate.
- You need to download and install your new certificate within 72 hours of re-keying your certificate to keep your server secure when the old certificate is terminated.
- Go to your Wurk product page.
- Select SSL Certificates and select Manage for the certificate you want to rekey.
- Select Rekey your certificate.
- In the Certificate Signing Request (CSR) field, paste your new CSR, including ----BEGIN NEW CERTIFICATE REQUEST---- and ----END CERTIFICATE REQUEST----, and then select Add Change.
- Select Submit All Changes.
Your newly re-keyed certificate will become available shortly after submitting the new CSR, and we'll email you when the certificate is available.
Next steps
- After you receive the issuance email, you need to download your newly keyed certificate.
- You must install the SSL certification within 72 hours of issuance to keep your server secure.
More info
- During the re-key process, you may have to verify your certificate request You'll get an email from us if this is necessary.
- If you're using a standalone SSL certificate on a Managed WordPress plan, follow the directions in Re-key my Managed WordPress standalone SSL certificate.
Where's my private key?
When you generate a CSR to request an SSL certificate to request an SSL certificate a private key is created on your local server. You shouldn't ever send your private key to someone else (including us!), but you'll need to know where it is to complete the installation of your SSL certificate. Below are some common places to find the private key on your server.
Windows/IIS
On Windows servers, the OS manages the certificate for you in a hidden file, but you can export a .PFX file that contains both the certificate and the private key.
- Open the Microsoft Management Console (MMC).
- In the Console Root, expand Certificates (Local Computer). Your certificate will be located in the Personal or Web Server folder.
- Locate and right click the certificate, click Export and follow the guided wizard.
Once you have the .pfx file, you can keep it as a backup of the key, or use it to install the certificate on another Windows server. If you're trying to use the certificate on a different OS, you'll need to split the .pfx into the certificate and the private key.
Apache
You can find the location of your private key in your Apache configuration file, which is named .httpd.conf or apache2.conf. The line SSLCertificateKeyFileshows you the file path to your private key.
NGINX
The path to your private key is listed in your site's virtual host file. Navigate to the server block for your site (by default, it's located in the /var/www directory). Open the configuration file for your site and search for ssl_certificate_key which will show the path to your private key.
More info
- Still can't find your private key? Try searching for a ".key" file, or following the installation steps for your server type. The installation steps should include where your private key is located.
- If your private key is nowhere to be found, or your site isn't serving HTTPS connections, you will need to rekey your certificate and save your private key in a location where you can find it.
What if I notice a problem with an SSL certificate?
Secure certificates are targets for different types of attacks and malicious behavior.
To report suspected private key compromise, certificate misuse, or other types of fraud, compromise, misuse, inappropriate conduct, or any other type of suspicious activity with a certificate, contact Starfield at practices@starfieldtech.com.
If your certificate is not working and you do not think it is fraud related, take a look at Test your SSL’s configuration.
Note: Starting June 1, 2021, Wurk will no longer issue or renew Code Signing or Driver Signing Certificates. If you already own a Code Signing or Driver Signing Certificate, you will be unable to rekey it after June 1, 2021. All certificates issued before June 1, 2021 will remain valid until they expire.
More info
- Install my SSL certificate
- Change the domain name (common name) on my SSL certificate
Change the domain name (common name) on my SSL certificate
You can change your SSL certificate's common name, which is the primary domain name that the certificate secures and encrypts. How you change your common name depends on where your certificate is currently hosted:
|
Hosting |
What to do |
|
Primary domain on a Wurk hosting account |
|
|
Websites + Marketing account |
|
|
Anywhere else |
Follow the steps below. |
- Go to your Wurk in product page
- Select SSL Certificates, and next to the SSL certificate you want to change, select Manage.
- Select Change the site that your certificate protects.
- Select one of the following based on where your website is hosted:
|
Hosting |
What to do |
|
Shared hosting or Site Builder |
Select Move your certificate to one of your hosted domains, and then select the domain name you want to use. |
|
Elsewhere |
Select Change to a different domain and enter the common name you want to use for the certificate. |
- Select Add Change.
- If you provided a Certificate Signing Request (CSR) from your server when you got your original SSL certificate and you're moving to a new server, you'll need to add an additional change to re-key the certificate with a CSR from the new server. Select Re-Key your certificate, paste the new CSR, and select Add Change.
- Select Submit All Changes.
Note: With Deluxe and Extended Validation SSLs, you can only change the common name, not the organization's information.
Related step
- Verify my SSL certificate request
More info
- Avoid the Chrome not secure warning
Need help? Find help in our knowledgebase or simply chat to us .
Wurk and its subsidiaries are registered services provider.